The 570Km range wasn't exactly supposed to be public. But then it was easily surmised based on regular published specs.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Nope, I never used any Microsoft provided source code or documentation. Heck the bit I reverse engineered could not have any documentation because it was an internal implementation part of windows SAM.Microsoft provides tool, documentation etc to help developers develop softwares to windows. But reverse engineering the source code itself is very difficult. The reactOS uses similar interface to make the appearance of Windows but is not same as Microsoft windows in real functioning. The clean room implementation is the process of making a software from scratch to mimic another software but does not make it identical. Though, reverse engineering is possible in areas which have not been encrypted
ReactOS can run original software written for Microsoft windows, un-altered. Even those which use undocumented APIs. If that is not 'real functionality' I don't know what is real functionality is.
And yes, encrypted software can be very easily reversed engineered. Almost all the malwares encrypt themselves. And they are routinely reverse engineered. The reason? You cann't execute an encrypted software, you will have to decrypt it before it is executed! That means both the encryption key and algorithm must be in that system somewhere! You can discover it and reverse engineer it, or even better use it as a cryptographic oracle and just decrypt the functional parts you want to analyse. This is the oldest problem with encryption, you have to decrypt a software to use it so encrypting it can only delay analsis by a week maximum.
Yes, the entire point of clean room implementation is to avoid charges of copyright violation. But thats the point! If you can reverse engineer something to the point that you know all its behaviour, you don't exactly need to produce verbatim copy of source code! You know what the software does and you can re-implement it in anyway you feel like.
More relevantly, incase of defence softwares embedded in a weapon or a platform, you don't need to re-implement the entire part. You only want to know how a particular thing is done. Or, if a particular black-box has a particular behaviour.
Encryption is usually worthless when it comes to reverse engineering protection. For encryption to hold any value, encryption algorithm or decryotion key should be unknown to the attacker. If you have to package both, well, its not exactly secure against reading. Embedded softwares are routinely reverse engineered, things like engine control units and its firmwares, control software for industrial equipments are easily reverse engineered.In case of objects like defence equipment, the software is also combined with hardware actuators. So, exact algorithm is hard to obtain just by observation. Also, the software tends to be encrypted t ensure reverse engineerring is not done by any third party. Nevertheless, a good idea can be obtained about the functioning of the equipment by observation and algorithm can be written in clean room to get a similar alternative.
However, dormant features like kill switch is very hard to find as actual reverse engineering is not easy (unless a bug or exploit is found). In addition, rewriting a code by replacing the original code is very hard as coordination with hardware has to be exact. It is easier to simply study the system, find the patterns, working of the system and then design a system inhouse to replicate those features but with own code, not reverse engineered code.
So, reverse engineering by study is possible but exact copy paste of source code is too hard as many critical items have encrypted software. But this studying and implementation requires highly experienced people and at least 10 years of experience working in the field
Ummm... Sorry to sound rude, but have you ever loaded a piece of code -- like a DLL or EXE or SO or a ROM dump or a firmware .BIN file into IDA?
It tells exactly under what condition any chunk of code will be executed. It logically groups bunch of instructions into blocks and tell when and what will cause an instruction to execute. There is nothing exactly 'active' or 'dormant' in a reverse engineering.
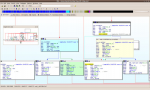
See all these lines? They represent the flow of control and conditions upon which a particular piece of code will be executed. It does not matter if a code is executed or not. Heck if it is not executed at all under 'normal' circumstances, I will be very very very much interested to know what it does. This is very very simple statistical analysis.
And IDA is actually a very old tool. There has been a massive progress in this field.
Also when it comes to extracting software embedded inside hardware, you know what is the easiest route? Order a spare and reverse engineer existing part. It is again something which is done routinely. Where do you think all the 'Chinese copies' of Radars etc come from? I know many people who do decapping of ICs, for a small fee. And its not expesnive at all. Plus, don't forget, these weapons platform service for decades. What is 'hard' right now will be extremely easy 5 years from now. What is hidded inside your epoxy covered chip will be taken out quite easily in 5 years. Loss of reputation by discovery of kill switch will be much worse.
And no, the only issue is not to patch an exisiting flaw --deliberate or accidental. It is the risk of exposure. If a customer finds a such a kill switch and that information becomes public, you can kiss your sales of weapons platform good-bye.
If Russia were to supply a bugged S-400, they can bet India will either secretly blackmail Russia or publically screw their sales by making all the dirty tricks they have hid in the system to all other customers. No one will buy weapon for quite sometime from Russia. Plus Russia will lose their biggest customer.
First rule of business, do not mess with a small customer for the sake of bigger customer, espeically if your business has a component of reputation or your products have a high-touch business model. Meaning you sell few but those few are really expensive.
Moreover, the basic common sense: Will Russia provide China something like a backdoor? What if later China herself makes that knowledge public in a bid to destroy Russian export market and establish their own.
This entire thing makes no sense. May be unless you are @BMD.
Last edited:
Guidance is electronics though.Maintaining control, compactness of chemical, guidance etc are way different for a SAM/BMD than that of a space rocket or simple missile. Since the idea is to intercept enemy missile, it is important that India has more understanding of the working.
Anyhow reality is that India does have its own SAM system and does not rely solely on S400
So why buy the S-400?
Because Japan is a US ally with a pretty much completely aligned approach to foreign policy. If they saw the US, or a US ally, as a potential major enemy, they would not buy these systems.Japan is also nominally a space faring nation, a major industrialized nation and yet it buys US Patriot SAMs. Green lumber fallacy all over again.
Both. Russia knows how to beat them because it designed them and China knows how to beat them because it reverse engineers literally everything.Do remember these are two very very different statements.
1. Russia will, or rather can, compromise India's SAM.
2. Russian SAMs will not work against China BECAUSE China also possesses them.
May I ask which one are you arguing?
And then there is one another statement that you speak: China will share information on how to compromise S-400 with Pakistan.
Which is laughable to say the least.
They started developing drones with EW, but very few drones are actually equipped with EW, and even those that have EW, have a relatively poorly spec'd EW compared to say a Growler's NGJ or a top Russian system.*Ahem* they do.
After 2011, CIA started using drone with EW. Even then, CIAs drones are still vulnerable to F-14 and they high tail when they see F-14 coming.
Read the link that I provided in my post.
BTW, point still remains that incorporating kill-switches is not exactly easy even for likes of USA. Or to ground entire Iranian fleet when US tried too hard. And yes, you can a fight an enemy having same weapons as you even if both your weapons were built by same manufacturers.
Only if they're dumb weapons like AK-47s and howitzers.
India can learn technology from S400. India also knows to do reverse engineering to get the technology from imported items. The technology can then be used to upgrade Indian radars and missiles for Akash, QRSAM, AAD etc.Guidance is electronics though.
So why buy the S-400?
Imports is never a means to fight wars. It is a way of technology acquisition
In case of military electronics, there is a chance that the coding language used itself could be radically different from what other countries use. The compilers needed may be different, the way things are interpreted (architecture of processors) may be different. Reverse engineering windows is relatively easier as it is something that is universally used. However, in case of military equipment, the software and hardware are linked to each other and the encryption is both software as well as hardware based. One may figure it out but it will be very hard and take thousands of smart engineers over decade to find out.Nope, I never used any Microsoft provided source code or documentation. Heck the bit I reverse engineered could not have any documentation because it was an internal implementation part of windows SAM.
ReactOS can run original software written for Microsoft windows, un-altered. Even those which use undocumented APIs. If that is not 'real functionality' I don't know what is real functionality is.
And yes, encrypted software can be very easily reversed engineered. Almost all the malwares encrypt themselves. And they are routinely reverse engineered. The reason? You cann't execute an encrypted software, you will have to decrypt it before it is executed! That means both the encryption key and algorithm must be in that system somewhere! You can discover it and reverse engineer it, or even better use it as a cryptographic oracle and just decrypt the functional parts you want to analyse. This is the oldest problem with encryption, you have to decrypt a software to use it so encrypting it can only delay analsis by a week maximum.
Yes, the entire point of clean room implementation is to avoid charges of copyright violation. But thats the point! If you can reverse engineer something to the point that you know all its behaviour, you don't exactly need to produce verbatim copy of source code! You know what the software does and you can re-implement it in anyway you feel like.
More relevantly, incase of defence softwares embedded in a weapon or a platform, you don't need to re-implement the entire part. You only want to know how a particular thing is done. Or, if a particular black-box has a particular behaviour.
Encryption is usually worthless when it comes to reverse engineering protection. For encryption to hold any value, encryption algorithm or decryotion key should be unknown to the attacker. If you have to package both, well, its not exactly secure against reading. Embedded softwares are routinely reverse engineered, things like engine control units and its firmwares, control software for industrial equipments are easily reverse engineered.
Ummm... Sorry to sound rude, but have you ever loaded a piece of code -- like a DLL or EXE or SO or a ROM dump or a firmware .BIN file into IDA?
It tells exactly under what condition any chunk of code will be executed. It logically groups bunch of instructions into blocks and tell when and what will cause an instruction to execute. There is nothing exactly 'active' or 'dormant' in a reverse engineering.
View attachment 3248
See all these lines? They represent the flow of control and conditions upon which a particular piece of code will be executed. It does not matter if a code is executed or not. Heck if it is not executed at all under 'normal' circumstances, I will be very very very much interested to know what it does. This is very very simple statistical analysis.
And IDA is actually a very old tool. There has been a massive progress in this field.
Also when it comes to extracting software embedded inside hardware, you know what is the easiest route? Order a spare and reverse engineer existing part. It is again something which is done routinely. Where do you think all the 'Chinese copies' of Radars etc come from? I know many people who do decapping of ICs, for a small fee. And its not expesnive at all. Plus, don't forget, these weapons platform service for decades. What is 'hard' right now will be extremely easy 5 years from now. What is hidded inside your epoxy covered chip will be taken out quite easily in 5 years. Loss of reputation by discovery of kill switch will be much worse.
And no, the only issue is not to patch an exisiting flaw --deliberate or accidental. It is the risk of exposure. If a customer finds a such a kill switch and that information becomes public, you can kiss your sales of weapons platform good-bye.
If Russia were to supply a bugged S-400, they can bet India will either secretly blackmail Russia or publically screw their sales by making all the dirty tricks they have hid in the system to all other customers. No one will buy weapon for quite sometime from Russia. Plus Russia will lose their biggest customer.
First rule of business, do not mess with a small customer for the sake of bigger customer, espeically if your business has a component of reputation or your products have a high-touch business model. Meaning you sell few but those few are really expensive.
Moreover, the basic common sense: Will Russia provide China something like a backdoor? What if later China herself makes that knowledge public in a bid to destroy Russian export market and establish their own.
This entire thing makes no sense. May be unless you are @BMD.
One of the best examples is the reason USA doe not sell F22 - that it can jeopardise USA algorithms. But USA has developed F35 to be sold as exports desite being 5th generation due to presence of safeguards which prevent reverse engineering
That would then leave even more systems prone to Russian and Chinese EW and RF cyber warfare.India can learn technology from S400. India also knows to do reverse engineering to get the technology from imported items. The technology can then be used to upgrade Indian radars and missiles for Akash, QRSAM, AAD etc.
Imports is never a means to fight wars. It is a way of technology acquisition
Actually.... its not that hard to find what was the processor and coding language involved. I wanted to look at Tejas, here it is:In case of military electronics, there is a chance that the coding language used itself could be radically different from what other countries use. The compilers needed may be different, the way things are interpreted (architecture of processors) may be different. Reverse engineering windows is relatively easier as it is something that is universally used. However, in case of military equipment, the software and hardware are linked to each other and the encryption is both software as well as hardware based. One may figure it out but it will be very hard and take thousands of smart engineers over decade to find out.
One of the best examples is the reason USA doe not sell F22 - that it can jeopardise USA algorithms. But USA has developed F35 to be sold as exports desite being 5th generation due to presence of safeguards which prevent reverse engineering
(PDF) Flight Control Software: Mistakes Made and Lessons Learned
In the Indian Light Combat Aircraft (LCA) program the flight control laws and the Airdata algorithm is
coded in Ada language and compiled for an i960 processor using a qualified compiler.
It took me precisely 25 seconds to find this.
i960 is StrongARM processor from Intel. A very very common ISA for embedded system from 90s.
Language is Ada but that is not even needed for even someone like me --who is not a professional-- to reverse engineer.
If I can get hold of binary of Tejas's flight control laws, I can easily give you its algorithm in less than an hour. And I am not even a halfway decent reverse engineering person.
You are speaking of just FBW without considering the complex radar and other electronics. The FBW is not something that will have complexities. The other electronics will have. The black box or kill switch is kept connected to antennaes and radars so as to get the signals and apply the kill command.Actually.... its not that hard to find what was the processor and coding language involved. I wanted to look at Tejas, here it is:
(PDF) Flight Control Software: Mistakes Made and Lessons Learned
It took me precisely 25 seconds to find this.
i960 is StrongARM processor from Intel. A very very common ISA for embedded system from 90s.
Language is Ada but that is not even needed for even someone like me --who is not a professional-- to reverse engineer.
If I can get hold of binary of Tejas's flight control laws, I can easily give you its algorithm in less than an hour. And I am not even a halfway decent reverse engineering person.
Well, pop quiz. Do you know which are among the most complex piece of software? By complex, I mean having the most number of parts. Its not radar firmwares is something I can assure you. Remember, specialized things are not necessarily complex.You are speaking of just FBW without considering the complex radar and other electronics. The FBW is not something that will have complexities. The other electronics will have. The black box or kill switch is kept connected to antennaes and radars so as to get the signals and apply the kill command.
One more thing, those 'extremely complex' softwares, are routinely reverse engineered.
Last edited:
Things like Growler will work against practically any radar, not specifically F-14's radar.They started developing drones with EW, but very few drones are actually equipped with EW, and even those that have EW, have a relatively poorly spec'd EW compared to say a Growler's NGJ or a top Russian system.
Only if they're dumb weapons like AK-47s and howitzers.
If USA had some inbuilt kill-switches, they would have used to ground and destroy Iran's F-14s. Heck using the drones as well. Exchanging a drone for a F-14 AND its pilot is a good exchange. Remember USA went out of its way to deny Iran its F-14 fleet by blocking spares and punishing those who were selling spares. Even if they were in other countries. When it comes to Iran, US takes things very very seriously.
BTW, Also the fact that Iran was targetted using 'cyber weapons' -- I hate the word 'cyber'.
The point is, having space capabilities does not mean you will NOT buy SAMs from a foreign party. Both are unrelated.Because Japan is a US ally with a pretty much completely aligned approach to foreign policy. If they saw the US, or a US ally, as a potential major enemy, they would not buy these systems.
Wait, now this is interesting.Both. Russia knows how to beat them because it designed them and China knows how to beat them because it reverse engineers literally everything.
Do you believe China will be able to defeat Indian S-400s because they can reverse engineer S-400 or find its limits by experimentation OR Do you believe Russia will hand them over ways to defeat S-400.
Former is possible, later is not.
That said for former, India will be doing exactly that too and will know what China knows.
Both. Basically your air defence is screwed by either or both, making it a dumb purchase.Wait, now this is interesting.
Do you believe China will be able to defeat Indian S-400s because they can reverse engineer S-400 or find its limits by experimentation OR Do you believe Russia will hand them over ways to defeat S-400.
Former is possible, later is not.
That said for former, India will be doing exactly that too and will know what China knows.
It does if, as someone said, you intend replacing all the electronics anyway. Which is not what Japan is doing.The point is, having space capabilities does not mean you will NOT buy SAMs from a foreign party. Both are unrelated.
And how is it not dumb purchase for China then?Both. Basically your air defence is screwed by either or both, making it a dumb purchase.
You know, both India and Turkey will be having this system.
And both will know everything that China knows.
They probably didn't in the 1970s, but if the Iranians are still using the same radar, EW and AAMs + electronics, they would be screwed. Well, F-22 means they're screwed anyway, so all this is irrelevant. I doubt the US feels very threatened by a '70s fighter jet in the year 2018.Things like Growler will work against practically any radar, not specifically F-14's radar.
If USA had some inbuilt kill-switches, they would have used to ground and destroy Iran's F-14s. Heck using the drones as well. Exchanging a drone for a F-14 AND its pilot is a good exchange. Remember USA went out of its way to deny Iran its F-14 fleet by blocking spares and punishing those who were selling spares. Even if they were in other countries. When it comes to Iran, US takes things very very seriously.
BTW, Also the fact that Iran was targetted using 'cyber weapons' -- I hate the word 'cyber'.
Because China actually does reverse engineer and then copy everything and they're too big for Russia to get annoyed at them for doing it - see HQ-9. They're probably also secretly doing research into beating Russian air defences. Turkey is getting it so that NATO can analyse it.And how is it not dumb purchase for China then?
You know, both India and Turkey will be having this system.
And both will know everything that China knows.

